Whereas the web has dramatically expanded the flexibility to share information, it has additionally made problems with privateness extra sophisticated. Many individuals are justifiably frightened about their private data being stolen or seen, together with financial institution information, bank card data, and browser or login historical past.
Should you’re searching for extra privateness whereas searching, Tor is an effective method to do this, as it’s software program that permits customers to browse the net anonymously. It needs to be famous that Tor can be utilized to entry unlawful content material on the darkish net, and Digital Traits doesn’t condone or encourage this habits.
Why does Tor exist?
On this local weather of information gathering and privateness considerations, the Tor browser has turn into the topic of debate and notoriety. Like many underground phenomena on the web, it’s poorly understood and shrouded within the kind of technological mysticism that individuals usually ascribe to issues like hacking or Bitcoin.
Initially developed by the U.S. Naval Analysis Lab within the Nineteen Nineties, onion routers get their identify from the onion-like layering approach that conceals details about consumer exercise and site. Maybe sarcastically, the group obtained the majority of its funding from branches of america authorities for years, which nonetheless views Tor as a device for fostering democracy in authoritarian states.
To know how Tor can defend a consumer’s identification as they browse the web, we have to focus on the web. At its most elementary, it’s a collection of connections between computer systems throughout nice distances. Some PCs home the info saved on the web, together with webpages like Google, that are often called servers. A tool used to entry this data, corresponding to a smartphone or PC, is called a consumer. The transmission traces that join purchasers to servers are available in quite a lot of types, whether or not fiber-optic cables or Wi-Fi, however they’re all connections. With the invention of Wi-Fi, satellite tv for pc web, and moveable hotspots, the web is each extra accessible and extra susceptible than ever earlier than.
Knowledge might be intercepted or spied on in a rising number of methods, particularly if networks should not utilizing correct encryption or have unintentionally downloaded malware. On the white hat aspect, people and organizations (together with governments, legislation enforcement ISPs, and social media corporations) can entry web information to observe who’s performing unlawful actions — or to gather beneficial information on consumer behaviors and actions that may be analyzed or offered.
A rising variety of options deal with these privateness points, corresponding to VPNs or Digital Non-public Networks. Tor is one other browser-based answer that many use.
How Tor has the reply to safe searching
There are two vital elements of onion routing. First, the Tor community consists of volunteers who use their computer systems as nodes. Throughout regular searching, data travels throughout the web in packets. When a Tor consumer visits an internet site, nonetheless, their packets don’t instantly transfer to that server. As a substitute, Tor creates a path by way of randomly assigned nodes that the packet will observe earlier than reaching the server.
The opposite essential side of onion routing is how the packets are constructed. Usually, packets embody the sender’s deal with and the vacation spot, like snail mail. When utilizing Tor, packets are as an alternative wrapped in successive layers like a nesting doll.
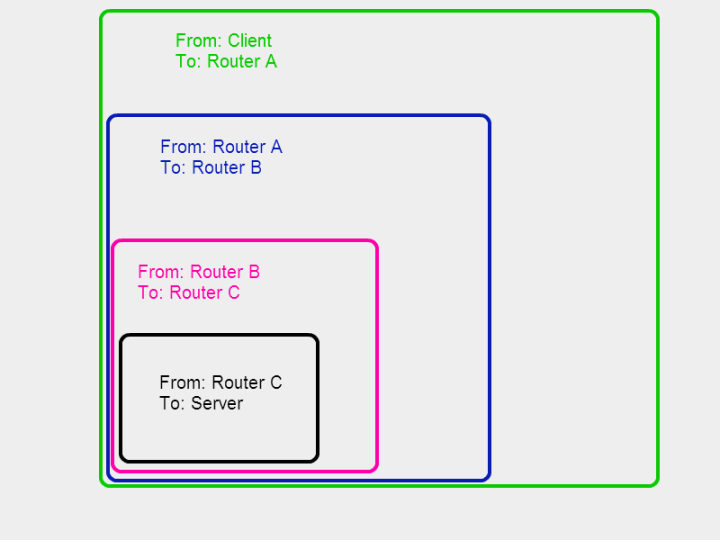
When the consumer sends the packet, the highest layer tells it to go to Router A, the primary cease on the circuit. When it’s there, Router A takes off the primary layer. The following layer instructs Router A to ship the packet to Router B.
Router A doesn’t know the last word vacation spot, solely that the packet got here from the consumer and went to B. Router B peels off the subsequent layer, passing it down the road to Router C, and this course of continues till the message reaches its vacation spot.
At every cease, the node solely is aware of the final place the packet was and the subsequent place it is going to be. No node information the whole path of information, and neither would anybody observing the message exit, assuming your first three servers are configured appropriately.
Who makes use of Tor, and why?
Anonymity is Tor’s bread and butter, and as such, it’s most likely inconceivable to get an correct view of its consumer base. Particular developments turn into obvious, nonetheless, and a few Tor advocates are particularly vocal about their causes for utilizing the service.
Tor has turn into standard with journalists and activists in nations that impose restrictions on their citizen’s web and expression. For whistleblowers, Tor offers a protected avenue to leak data to journalists.
You won’t know, however when Edward Snowden launched data on the NSA’s PRISM program to information organizations, he did so through Tor. One doesn’t must be an activist, freedom fighter, or legal to understand Tor, nonetheless. Many teachers and strange residents endorse Tor as a device to maintain privateness and freedom of expression alive within the digital age. Businesses just like the CIA are additionally energetic on Tor to make it simpler to obtain ideas and knowledge.
Regardless of the Tor Venture’s good intentions, Tor has developed a foul repute within the mainstream press, and never with out trigger. When you have got a free-to-use privateness browser that’s simply distributed and affords customers each help and neighborhood boards, it’s no shock that a few of these communities kind round disreputable topics. Tor fights again in opposition to this connotation with PrivChat webinars from a few of its standard customers in human rights and pushes for democracy, in addition to guides for these working below hostile governments to assist them keep protected.
The way to use Tor: the way to get it
In step with the ideological goals of the Tor Venture, Tor is free to make use of and obtainable throughout most platforms, together with Linux. Merely obtain and set up the browser from the Tor Venture web site, which is a modified model of Firefox obtainable for Home windows, macOS, Linux, and Android.
Customers ought to observe that whereas Tor Browser is pre-configured to work appropriately, customers on networks with firewalls or different safety techniques could expertise difficulties. Furthermore, being careless when searching can nonetheless compromise one’s anonymity. Tor’s web site has a listing of issues to keep away from doing whereas utilizing the browser.
The way to use Tor: a fast tour of the software program
When you’ve downloaded and put in Tor Browser, you’ll must know the way to navigate it. Observe these steps for a fast tour of Tor Browser:
Step 1: Open Tor Browser in your PC.
Step 2: On the Hook up with Tor display screen that seems, you’ll be able to both go forward and connect with Tor by deciding on Join or take the time to arrange your connection by selecting the Configure connection possibility. For the aim of this information, we’re going to only select Join.
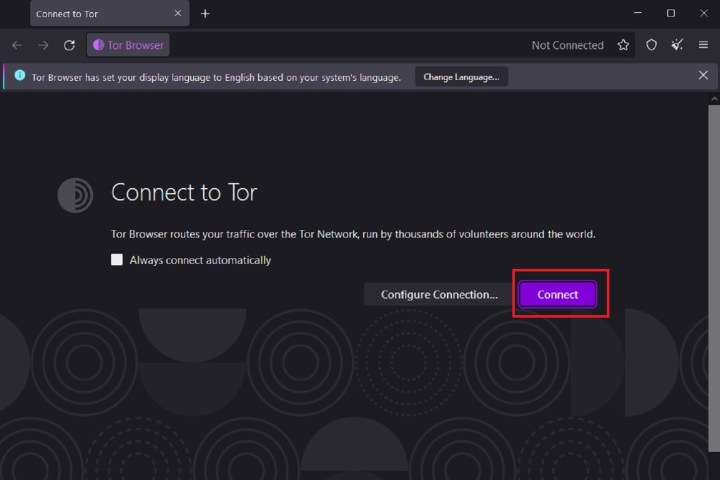
Step 3: It might take a couple of minutes to attach, however when you’re related to Tor, you’ll be introduced with a welcome display screen that contains a DuckDuckGo search engine search bar prominently. You should use this search bar or the one on the prime of your Tor Browser window to carry out a extra personal net search. To take action within the deal with bar on the prime of your display screen, simply kind in your search phrases and press the Enter key in your keyboard or choose the Proper arrow icon within the deal with bar. It’s best to then be introduced with a DuckDuckGo search outcomes web page.
Step 4: Should you’ve used Firefox earlier than, Tor Browser will look acquainted to you:
- You’ll nonetheless choose the Star icon to bookmark a webpage.
- You’ll nonetheless use the deal with bar on the prime of the window to conduct net searches, and sort in net or onion addresses for sure web sites. And also you’ll choose the Plus signal icon to open new tabs.
- The Three horizontal traces menu icon will nonetheless open a bigger menu of options and settings on your browser, however it’ll additionally comprise some new Tor-specific options corresponding to New identification and New Tor circuit for this website. We’ll go over these and different new options within the following steps.
Step 5: Some web sites are onion providers, which implies you’ll be able to solely entry these websites through the Tor community. To get to those onion service web sites, you’ll normally must kind of their onion deal with into the deal with bar on the prime of the Tor Browser’s window. This deal with is normally 56 characters lengthy and ends with a “.onion”. Some common web sites additionally supply an onion service model of their website. In the event that they do, Tor will normally present a purple “.onion obtainable” icon within the deal with bar. You may choose this to open the onion service model of an internet site.
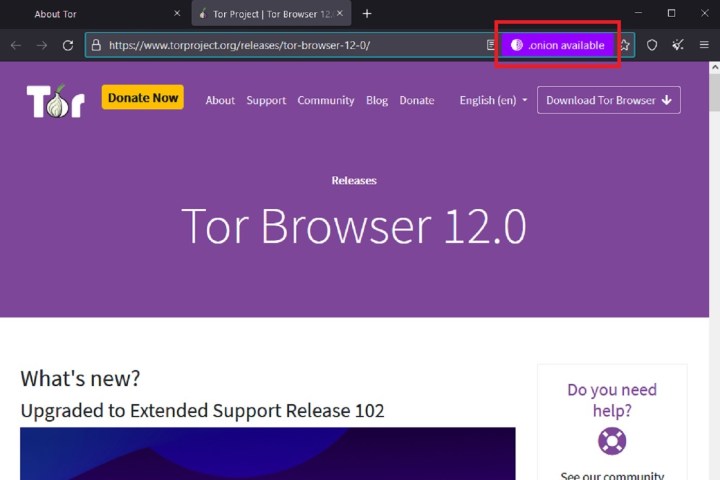
Step 6: There are two icons within the prime proper nook of the Tor Browser, positioned between the menu icon and the Star bookmark icon: a defend icon and a brush icon. If you choose the Defend icon, you’ll be able to select the safety stage of your searching expertise. The Broom icon signifies the New identification function which permits customers to start out a totally new session and wipes all traces of the previous/present session by closing all home windows and tabs, and deleting all personal data like searching historical past. Tor Browser primarily restarts.
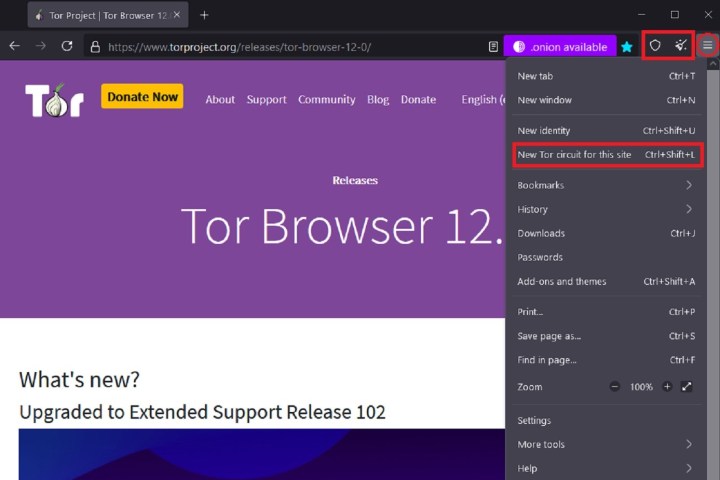
Step 7: If you choose the Three horizontal traces menu icon, a drop-down menu will seem. In that menu, alongside New identification, you can too choose New Tor circuit for this website. A circuit is basically the pathway it takes to attach a consumer to an internet site through Tor. Should you’re having hassle connecting to an internet site, you’ll be able to restart the tab and attempt to load the web site with a brand new circuit as a way to set up a profitable connection. You are able to do this by deciding on the New Tor circuit for this website possibility. Your personal data doesn’t get deleted with this function.
Exploring the deep net

Tor is effective as a device to guard the consumer’s privateness, however that’s not its solely helpful perform. The opposite, extra notorious use for Tor is as a gateway into the deep net, the huge portion of the net that’s not listed by engines like google. One other standard time period, darkish net, usually refers to all of the unlawful or troubling exercise that may occur on the deep net, however the two aren’t essentially interchangeable, and customers can trawl the deep net with out nefarious intent.
Tor permits webpages, like purchasers, to guard their anonymity by configuring a server to attach with purchasers at a Tor relay in between. The server doesn’t want to offer the IP deal with, and the consumer doesn’t want it, as an alternative utilizing an onion deal with, a 56-character code that purchasers enter rather than a standard URL.
The hidden pages on the Tor community comprise one of the vital well-known darknets, that are networks solely accessible by way of specific software program or authorization. A phrase like “darknet” conjures up photographs of shady dealings and never with out trigger. A few of the most notable hidden websites visitors in unlawful items and providers, just like the Silk Street, which was a well-liked black market darknet shut down by the FBI in 2013.
What are Tor’s limitations, hazards, and basic security?

Whereas Tor is beneficial for searching the net anonymously, it’s not with out issues. Naturally, this has drawn the eye of presidency organizations just like the NSA and FBI, who take into account Tor a goal of specific curiosity.
Whereas the Tor community is safe from visitors evaluation, Tor is a modified model of Firefox and is susceptible to assaults and exploits like another browser. By infecting somebody’s pc with malware, governments and cybercriminals can observe browser actions, log keystrokes, copy webcam and surveillance footage, and even remotely entry and management internet-connected gadgets.
There is no such thing as a technique to be utterly safe on the web, and Tor doesn’t change this. By taking affordable precautions, it’s attainable to reduce the dangers of searching with Tor, like utilizing the TorCheck web site to test that your connection to Tor is safe. You too can incorporate a digital personal community or VPN to offer extra safety on your digital actions.
An essential caveat to recollect is that since Tor is free and open-source software program, it isn’t capable of defend any private data that you just select to enter right into a kind. Similar to at all times, that you must use frequent sense when searching the web and sharing data.
Additionally understand that customers could must disable sure scripts and plugins, so it’s possible you’ll not have the ability to run every part you need on Tor. And if you happen to’re desirous about utilizing Tor to obtain torrents, assume once more. Torrenting is a file-sharing course of that depends on the P2P protocol. Customers obtain bits of a file from others and share the bits they’ve acquired with customers who’re downloading the identical file. This protocol makes your IP deal with seen to the customers you share information with, making onion routing pointless.
Should you resolve to go to Tor’s hidden or nameless servers, be conscious of the websites you go to. Whereas many pages are usually socially acceptable or on the very least authorized, corresponding to websites for whistleblowers or Bitcoin exchanges, a number of the different websites are havens for disturbing and even legal habits.
Editors’ Suggestions


